user object, a context object, and a callback function.
function MyRule1 (user, context, callback) {...}). To learn more, read Error Handling Best Practices.
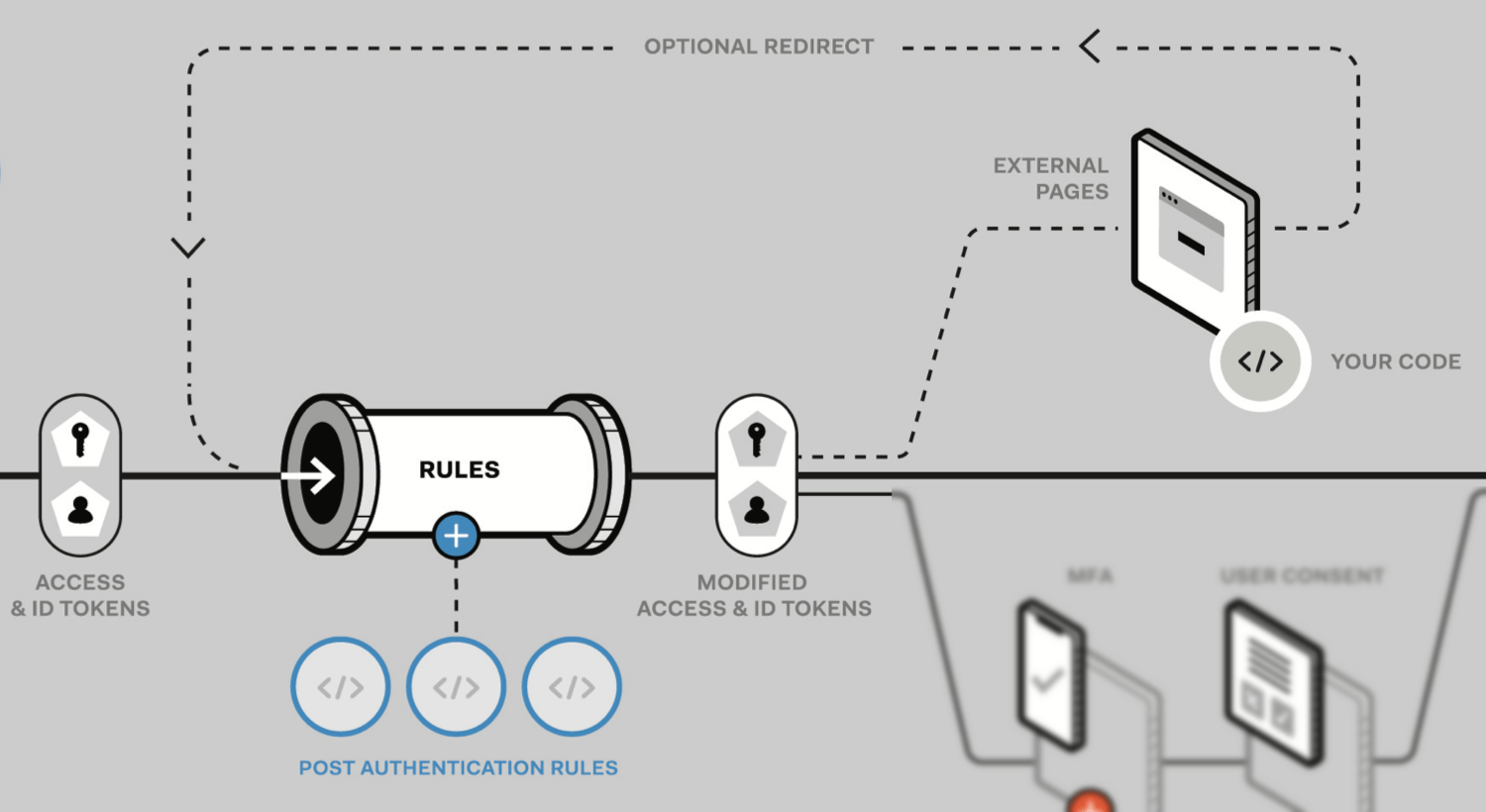
Rules execute in the pipeline associated with the generation of artifacts for authenticity that forms part of the overall Auth0 engine. When a pipeline is executed, all enabled rules are packaged together in the order in which they are listed and sent as one code blob to be executed as an Auth0 serverless Webtask. To see the entire Auth0 engine, download Inside the Auth0 Engine.
Size
We recommend that the total size of implementation for all enabled rules should not exceed 100 kB. The larger the size, the more latency is introduced due to the packaging and transport process employed by the Auth0 serverless Webtask platform, and this will have an impact on the performance of your system. Note that the 100 kB limit does not include anynpm modules that may be referenced as part of any require statements.
Order
The order in which rules are displayed in the dictates the order in which the rules will be executed. This is important because one rule may make one or more definitions within the environment associated with execution that another rule may depend upon. In this case, the rule making the definition(s) should execute before the rule that makes use of it. To learn more, read Rules Environment Best Practices. Run expensive rules that call APIs (including the Auth0 ) as late as possible. If you have other, less expensive rules that could cause anunauthorized access determination, then you should run these first.

