Custom Token Exchange is currently in Early Access for Enterprise customers only. Reach out to your Auth0 contact to request access. To learn more about Auth0’s product release cycle, read Product Release Stages.
/oauth/token endpoint. This is useful for advanced integration use cases, such as:
- Get Auth0 tokens for another
- Integrate an external
- Migrate to Auth0
subject_token_type, which provides information about the user for the transaction, and an Action. In that Action, you can write custom code to decode and validate subject tokens passed to the /oauth/token endpoint.
You can use Custom Token Exchange to authenticate users. For example, in an Action, you can apply the authorization logic for your use case and set the user for the transaction. Auth0 will then issue access, ID, and for the user.
Custom Token Exchange gives you the added flexibility to set the user for the transaction by taking on the additional responsibility of securely validating the corresponding subject token that identifies the user for the transaction.Remember that subject tokens used with Custom Token Exchange can be any token format or type you require, as long as your Action code can interpret them. You must implement strong validation of the tokens you receive and accept. If you fail to do so, you open yourself up to different attack vectors, such as spoofing or replay attacks, resulting in bad actors being able to authenticate with someone else’s user ID.To learn about different options for implementing secure validation of your subject tokens, read and apply the recommendations included in Example Use Cases and Code Samples. Make sure you also take into consideration and apply Attack Protection capabilities.
Setup
Application
To use Custom Token Exchange, you must create a new application with the or the . You can create multiple applications to use Custom Token Exchange. When you create a new application:- By default, Custom Token Exchange is disabled. To enable Custom Token Exchange, use the Management API to make a POST call to Create a Client or a PATCH call to Update a Client. Set the
allow_any_profile_of_typeattribute undertoken_exchangeto["custom_authentication"]:
- Enable the database connection or enterprise connection you want to use with Custom Token Exchange for the application.
- Make sure your application is flagged as First-Party and it is configured as OIDC Conformant in Dashboard > Applications > Advanced Settings > OAuth.
Custom DBs with Import Users to Auth0 enabled are only supported for
setUserById operations.client_id and client_secret for later use when calling the /oauth/token endpoint.
Custom Token Exchange Profile
Each Custom Token Exchange Profile maps to asubject_token_type and is associated with an Action that contains the code logic for that use case.
Custom Token Exchange requests sent to the /oauth/token endpoint with a specific subject_token_type value map to the corresponding Custom Token Profile and route to the associated Action for processing.
To create a Custom Token Exchange Profile, first create an Action for the profile.
Create Action
In the Auth0 Dashboard:- Navigate to Actions > Library.
- Select Create Action > Build from Scratch.
- In the Create Action dialog, enter a name and select the Custom Token Exchange trigger from the drop-down.
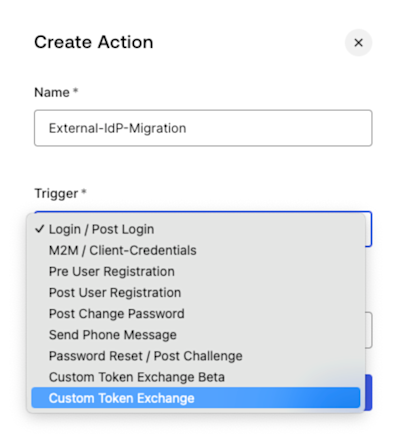
- Select Create.
- Deploy the Action.
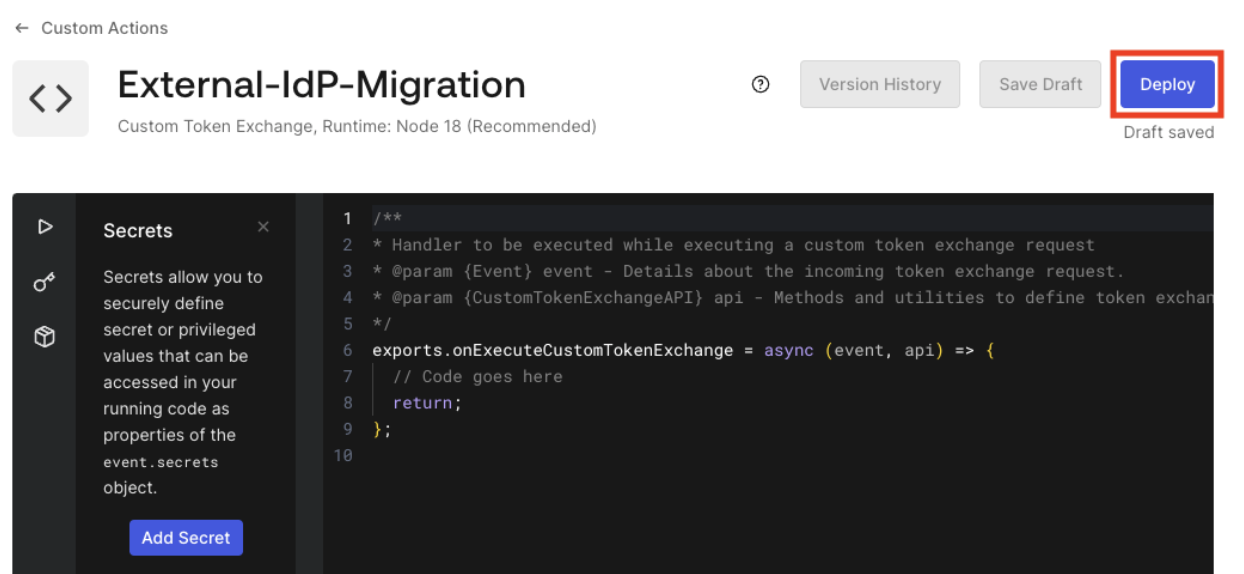
- To get the Action ID in the Auth0 Dashboard, navigate to the URL of the browser window. The Action ID should be the last part of the URL, as shown in the following image:
/actions endpoint:
actions[0].id. You need the Action ID to create the Custom Token Exchange Profile.
Create the Custom Token Exchange Profile
To create the Custom Token Exchange Profile, use the Management API to make a POST request with the following parameters to the/token-exchange-profiles endpoint:
| Parameter | Description |
|---|---|
subject_token_type | Unique profile token type URI starting with https:// or urnThe following namespaces are reserved and you can’t use them:
|
action_id | Action ID of Action associated with the Custom Token Profile. |
type | Should be set to custom_authentication. |
Manage Custom Token Exchange Profile
To manage your Custom Token Exchange Profile, use the Management API to make requests to the/token-exchange-profiles endpoint.
To get all your Custom Token Exchange Profiles, make the following request. This endpoint supports checkpoint pagination in case you have several profiles.
name or subject_token_type of a Custom Token Exchange Profile, use the following PATCH request. You cannot modify the Action ID, although you can change the custom code it executes with the Actions editor:
Actions API
Custom Token Exchange vs Post Login Action
The Custom Token Exchange Action, available as a part of Custom Token Exchange Early Access, can use the new API methods listed in Use the Actions API. For other needs, such as adding custom claims to , your Post Login Actions trigger executes after the Custom Token Exchange Action runs for the user that you set for the transaction, thus giving you the same functionality as other login flows. To identify a transaction that uses the token exchange grant type, look for anevent.transaction.protocol value equal to oauth2-token-exchange in your Post Login Action. Because the token exchange grant type is used by both the Custom Token Exchange and Native Social Login transactions, you can use the value of the subject_token_type to distinguish between the two, where the subject_token_type corresponds to one of your Custom Token Exchange Profiles.
Custom Token Exchange Early Access does not support multi-factor authentication. Enabling MFA as a tenant policy or using
api.multifactor.enable(), api.authentication.challengeWith(), or api.authentication.enrollWith() is not yet supported for Custom Token Exchange and, within your Post-Login Action trigger, will result in the transaction failing with a non-recoverable error. Make sure you skip enabling MFA when event.transaction.protocol==oauth2-token-exchange depending on the subject_token_type value.MFA support will be added in next iterations of Custom Token Exchange EA.Use the Actions API
Auth0 provides a number of API methods to use with your Token Exchange Action. You should implement an Action that decodes and validates the subject token based on thesubject_token_type. This will provide you with information about the user for the transaction. With this information, your code should also enforce the authorization policy needed for the transaction. Once you are sure the transaction can proceed, you can confirm it by setting the corresponding user. Auth0 will then issue access, ID, and refresh tokens for this user. You can think of this as a way to authenticate users.
Each Custom Token Exchange transaction generates a tenant event log. Successful transactions generate event logs of type secte, while failed transactions generate event logs of type fecte. Use these log types to help you understand any errors you may receive. Errors from the /oauth/token endpoint reveal less details.
Custom Token Exchange gives you the added flexibility to set the user for the transaction by taking on the additional responsibility of securely validating the corresponding subject token that identifies the user for the transaction.Remember that subject tokens used with Custom Token Exchange can be any token format or type you require, as long as your Action code can interpret them. You must implement strong validation of the tokens you receive and accept. If you fail to do so, you open yourself up to different attack vectors, such as spoofing or replay attacks, resulting in bad actors being able to authenticate with someone else’s user ID.To learn about different options for implementing secure validation of your subject tokens, read and apply the recommendations included in Example Use Cases and Code Samples. Make sure you also take into consideration and apply Attack Protection capabilities.
api.authentication.setUserById(user_id)
Sets user attributes based on a specified user ID for any connection type. This allows you to specify an existing user without updating the profile. This method fails if the user does not exist or is blocked.| Parameter | Description |
|---|---|
user_id | The user ID, such as auth0|55562040asf0aef. |
api.authentication.setUserByConnection(connection_name, user_profile, options)
Sets a user and their associated profile attributes in a specified connection. This is equivalent to returning the specified user profile from the federated IdP (or the corresponding Custom DB with Import Users to Auth0 disabled) when a user logs into this connection. You can configure whether this operation should create the user if it does not exist, and whether it should update the profile using the provided user profile attributes. The login count will be incremented for each user that is logged in viasetUserByConnection(). This method always fails for blocked users.
Custom Token Exchange EA currently supports
setUserByConnection() for Auth0 database connections, Enterprise and Social connections, and Custom DBs with Import Users to Auth0 disabled.| Parameter | Description |
|---|---|
connection_name | The name of the connection where the user profile will be set. Limited to 512 characters. |
user_profile | An object containing the user profile attributes to be set. Limited to 24 properties. |
options | An object specifying update and creation behavior.{updateBehavior: ‘replace’ | ‘none’,creationBehavior: ‘create_if_not_exists’ | ‘none’,}If the user exists, updateBahaviour does the following:
|
Supported user profile attributes
ThesetUserByConnection() method allows you to set profile attributes supported by the Update a User endpoint:
user_id(required): user’s unique identifier for this connection/provider. It is typically the user ID provided by the external identity provider for the connection. This is the only required parameter when bothcreationBehaviourandupdateBehaviourare set tonone.emailemail_verified. Defaults tofalse.usernamephone_numberphone_verified. Defaults tofalse.namegiven_namefamily_namenicknamepicture
Supported connection strategies
The current version provides support for the following connection strategies. ThesetUserByConnection() method fails for other strategies. Please contact Auth0 support to request adding support for other strategies.
Auth0 database connections:
- Custom database connections with Import Users to Auth0 disabled
- Custom Social Connections
- Apple
- Github
- Windowslive
Creation behavior
Users are dynamically created only whencreationBehavior is set to create_if_not_exists.
When creating users:
- You must provide an identifier as configured by your connection. By default, an email is required.
- For connections that use Flexible Identifiers and Attributes, you may provide a username and phone number if the corresponding attribute is enabled for the connection.
-
For connections that don’t use Flexible Identifiers and Attributes:
- You must provide an email address.
-
You may provide a username when the connection’s Require Username is set to
true. To learn more, read Adding Username for Database Connections. -
You cannot provide a
phone_number.
- You may specify
email_verifiedandphone_verified.
Set
creationBehavior to none when you want to log the user in but don’t want to create the user if they do not already exist in the connection.Future iterations of Custom Token Exchange will make the email attribute optional dependent on the connection configuration.Update behavior
User profile is updated only whenupdateBehavior is set to replace.
The following attributes cannot be modified and Auth0 returns an error when trying to change its value:
emailusernamephone_numberemail_verifiedphone_verified
If you want to use
setUserByConnection() to update a user profile that already contains email, username, or phone_number attributes, you must pass these attributes with the same value they already have. Otherwise, the method returns an error. Additionally, this action does not update the upstream Enterprise/Social IdP or the Custom DB, so make your updates match the latest version of the profile on the IdP/Custom DB if you want them to be in sync.Set
updateBehavior to none when you want to log the user in but don’t want to change any profile attributes if they already exist in the connection.Email verification
Auth0 automatically sends verification emails when you create a user withemail_verified=false. You can override this behavior by specifying verify_email=false as a user profile attribute. It won’t be stored as part of the user profile.
Set metadata
Unlike the Update a User endpoint, thesetUserByConnection() method does not allow you to set user or application metadata. Instead, you can use api.user.setAppMetadata. To learn how to correctly use metadata, read How Metadata Works in User Profiles. For metadata best practices, read How to Manage User Metadata with the Post-login Trigger.
api.user.setAppMetadata(name, value)
Sets application metadata for the user that is logging in. This method follows a merge behavior, so you can indicate the new attributes to add or the ones to be updated without affecting the existing ones. To remove an attribute, set its value tonull.
| Parameters | Description |
|---|---|
name | String. The name of the metadata property. |
value | String, object or array. The name of the metadata property. |
api.user.setUserMetadata(name, value)
Sets general metadata for the user that is logging in. This method follows a merge behavior, so you can indicate the new attributes to add or the ones to be updated without affecting the already existing ones. To remove an attribute, set its value tonull.
| Parameters | Description |
|---|---|
name | String. The name of the metadata property. |
value | String, object or array. The name of the metadata property. |
api.access.deny(code, reason)
Denies the login transaction and returns an error to the caller.| Parameter | Description |
|---|---|
code | A string returned in the error property in the response. Two standard error codes can be used:
If you use your own error code, it returns a 400 status code. |
reason | A string returned in the error_description property in the response. |
api.access.rejectInvalidSubjectToken(reason)
Denies the transaction and increments the counter of failed attempts for the external IP from which the request is coming. The Custom Token Exchange request is rejected with a400 Bad Request error response with the error code invalid_request.
When the maximum number of failed attempts is reached, Auth0 blocks traffic for a period of time for all Custom Token Exchange requests coming from that IP with a 429 Too Many Requests error response with error code too_many_attempts. To learn more read Attack Protection.
Use this method whenever you receive a Custom Token Exchange request with a subject token that is not properly signed/encrypted or expired, or under any circumstance that points to any non-legitimate usage such as in a spoofing or replay attack. This allows Auth0 to activate protection as per your configuration.
By default, Suspicious IP Throttling allows for 10 max attempts at a rate of 6 attempts/hour. To learn more, read Attack Protection.
| Parameter | Description |
|---|---|
reason | A string returned in the error_description property in the response |
api.cache
Store and retrieve data that persists across executions. These methods are useful for caching data used for subject token validation, such as public keys for signature validation. This can help improve performance when fetching the keys from ajwks-uri.
api.cache.delete(key)
Delete a record describing a cached value at the suppliedkey if it exists.
Returns a CacheWriteResult object with type: "success" if a value was removed from the cache. A failed operation returns type: "error". For errors, the returned object will have a code property that indicates the nature of the failure.
| Parameter | Description |
|---|---|
key | String. The key of the record stored in the cache. |
api.cache.get(key)
Retrieve a record describing a cached value at the suppliedkey, if it exists. If a record is found, the cached value can be found at the value property of the returned object.
Returns a cache record if an item is found in the cache for the supplied key. Cache records are objects with a value property holding the cached value as well as an expires_at property indicating the maximum expiry of the record in milliseconds since the Unix epoch.
Important: This cache is designed for short-lived, ephemeral data. Items may not be available in later transactions even if they are within their supplied lifetime.
| Parameter | Description |
|---|---|
key | String. The key of the record stored in the cache. |
api.cache.set(key, value, [options])
Store or update a string value in the cache at the specified key. Values stored in this cache are scoped to the Trigger in which they are set. They are subject to the Actions Cache Limits. Values stored in this way will have lifetimes of up to the specifiedttl or expires_at values. If no lifetime is specified, a default lifetime of 15 minutes will be used. Lifetimes may not exceed the maximum duration listed at Actions Cache Limits.
Returns CacheWriteSuccess if the values are stored successfully. Otherwise, you will receive CacheWriteError.
| Parameter | Description |
|---|---|
key | String. The key of the record stored in the cache. |
value | String. The value of the record to be stored. |
options | Optional object. Options for adjusting cache behavior. |
options.expires_at | Optional number. The absolute expiry time in milliseconds since the unix epoch. While cached records may be evicted earlier, they will never remain beyond the supplied expires_at.Note: This value should not be supplied if a value was also provided for ttl. If both options are supplied, the earlier expiry of the two will be used. |
options.ttl | Optional number. The time-to-live value of this cache entry in milliseconds. While cached values may be evicted earlier, they will never remain beyond the supplied ttl.Note: This value should not be supplied if a value was also provided for expires_at. If both options are supplied, the earlier expiry of the two will be used. |
Actions Event
In addition to new Actions API methods, you can use data in the Actions Event to learn about the context of the Token Exchange request, such as the subject token, IP address, client, and more.| Property | Type | Example |
|---|---|---|
| client | ||
client_id | string | HOVc2PDFTH7eahimN4yNCo8mOtjfNjLV |
name | string | My Web App |
metadata | object | {“foo”: “bar” } |
| tenant | ||
id | string | dev_1234 |
| request | ||
geoip | object | { … geoip object} |
hostname | string | dev_1234.us.auth0.com |
ip | string | 123.42.42.34 |
user_agent | string | Mozilla/5.0 |
language | string | en |
body | object | { // raw req.body } |
method | string | POST |
| transaction | ||
subject_token_type | string | urn://cic-migration-token |
subject_token | string | 41598922a1745f7af70 |
requested_scopes | string[] | [“openid”, “email”] |
| resource_server | ||
id | string | http://acme-api/v1/profile |
Deploy the Action
After you create your Token Exchange Action using the above API and Event objects, deploy the changes by clicking Deploy at the top of the page.
Call Token Exchange
To use Custom Token Exchange, make aPOST request to the /oauth/token endpoint with the following parameters. Remember that:
subject_tokensused with Custom Token Exchange can be any token format or type, as long as your Action code can interpret them.- Each
subject_token_typemaps to a specific Custom Token Exchange Profile and is associated with a specific Action that will be executed to control that transaction.
| Parameter | Description |
|---|---|
grant_type | For Custom Token Exchange, use urn:ietf:params:oauth:grant-type:token-exchange. |
subject_token_type | The type of the subject token. For Custom Token Exchange, this can be any URI scoped under your own ownership, such as http://acme.com/legacy-token or urn:acme:legacy-token.The following namespaces are reserved and cannot be used:
|
subject_token | The subject token, which your action should validate and use to identify the user. |
client_id | The client ID of the application you are using for the Token Exchange. As for other grant types, you can also pass the client ID in the Authorization header using HTTP Basic Auth. |
client_secret | The client secret of the application you are using for the Token Exchange. As for other grant types, you can also pass the client secret in the Authorization header using HTTP Basic Auth. Other alternatives are also available as explained in Auth0 Authentication API reference docs. Note Custom Token Exchange can be used by public Applications. Make sure to read Attack Protection in that case. |
audience | The API identifier defined in Auth0. |
scope | The OAuth2 scope parameter. |
event.request.body in the corresponding Action.
Organizations is not yet supported in Custom Token Exchange EA. Adding an organization parameter results in the request being rejected. Organizations support will be added in the next iterations of Custom Token Exchange.
Sample request
Attack Protection
To protect against spoofing and replay attacks, in which a tries to guess or reuse a subject token, Custom Token Exchange incorporates support for Suspicious IP Throttling. This enables you to specifically signal from your code in Actions when a subject token is invalid, so Auth0 can count the failed attempts sent from that external IP. When the number of failed attempts from an IP address reaches a pre-configured threshold, Auth0 blocks traffic for a Custom Token Exchange request coming from that IP with the following error:api.access.rejectInvalidSubjectToken in your Action code whenever the received subject token does not pass strong validation.
Suspicious IP Throttling is activated by default for Auth0 tenants. To learn more about how to (de)activate and configure it, read Suspicious IP Throttling. When activated, the default settings for Custom Token Exchange will be applied:
- Threshold: 10. Maximum number of failed attempts for an IP address.
- Throttling rate: 6 per hour. One additional attempt will become available after every 10 minutes until the threshold is refilled.
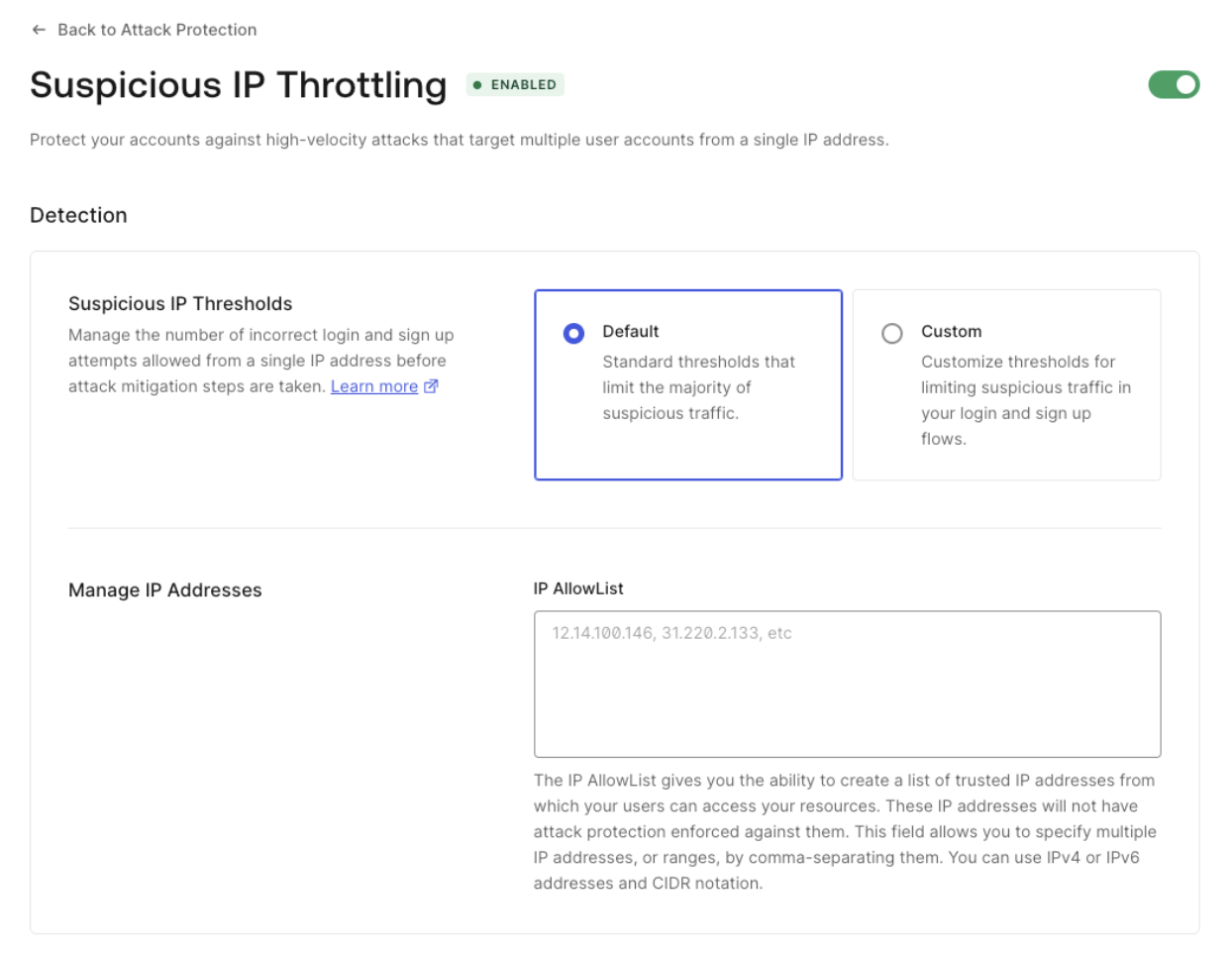
PATCH request to update the pre-custom-token-exchange stage with the needed values. Note that the rate is the interval of time in milliseconds at which new attempts are granted.
Example Use Cases and Code Samples
You can use Custom Token Exchange to solve advanced integration scenarios where normal federated login strategies based on redirecting the end user cannot be applied due to technical or user experience constraints. The code provided for the use cases is incomplete and only aims at showing the logical steps you can follow with your code to address the use case. Refer to code samples for more detailed code examples.Auth0 recommends using normal, out-of-the-box federated login whenever possible. By allowing you to set the user for the transaction, Custom Token Exchange gives you more flexibility by taking on the additional responsibility of securely validating and handling the transaction.
Use Case: Seamless migration into Auth0
GearUp has a mobile App used by millions of people and needs to modernize their Identity solution so they’ve decided to switch to Auth0. However, they want to avoid forcing users to re-authenticate as they migrate from their legacy identity provider, or IdP, as that adds friction to the user experience. To solve this, and to limit risks, GearUp is migrating incrementally. For each user, they wish to exchange the refresh token from their legacy IdP for an Auth0 access token, refresh token and set. This allows their app to seamlessly start using Auth0 as the IdP for this user, as well as consume GearUp APIs using Auth0-issued tokens. Once the exchange is done for all users, the app will be fully migrated and the old IdP can be disconnected–all without impacting end users and GearUp’s business.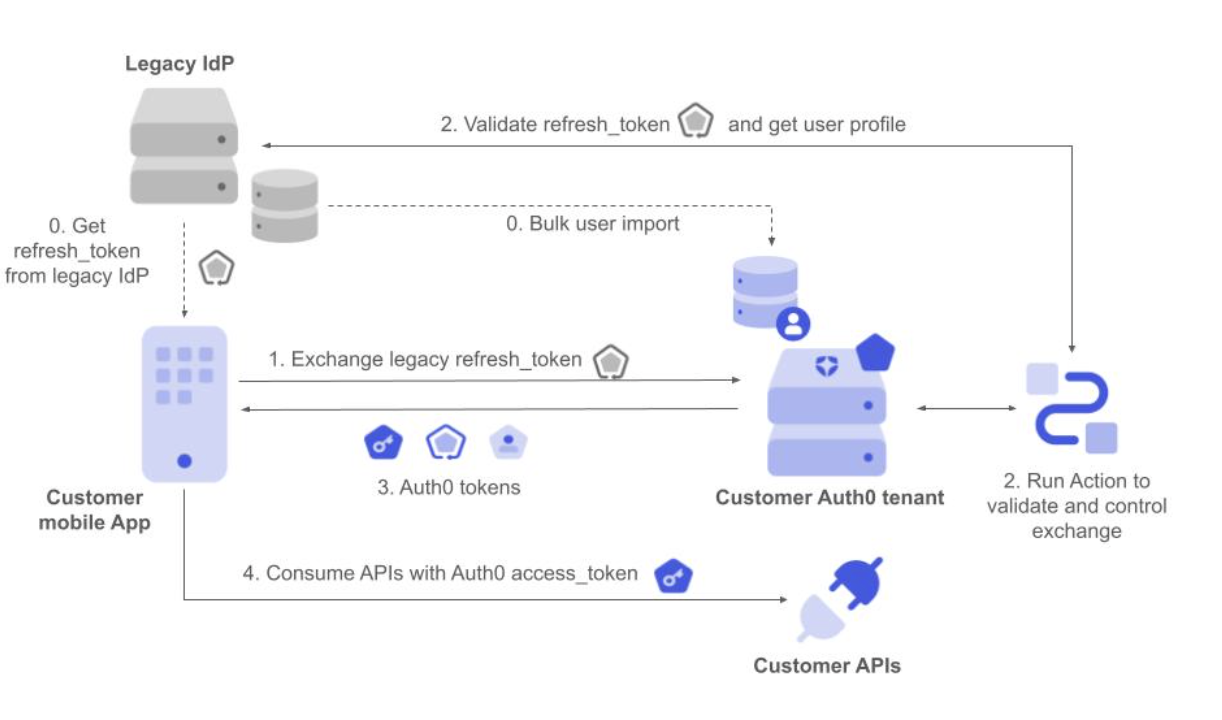
- The mobile app makes a request to Auth0 to exchange the legacy refresh token, setting it as the subject token.
- The corresponding Custom Token Exchange profile Action executes. It validates the refresh token with the legacy IdP and gets the external user ID from the user profile. It then applies the required authorization policy and finally sets the user.
- Auth0 responds with Auth0 access token, ID token, and refresh token.
- The mobile app can now use the Customer APIs using Auth0 tokens without the user having to re-authenticate.
- We don’t want to create the user.
- We don’t want to update the user profile.
Use Case: Re-use an external authentication provider
Another use case involves GearUp partnering with Air0, a leading travel provider, to offer their car rental services directly within the Air0 single-page application. GearUp offers a JavaScript library that encapsulates the use of their APIs. This way GearUp’s APIs can easily be consumed by Air0’s website where car rental services are being offered. Once again, the solution needs to be invisible to end users by avoiding re-authentication to GearUp. To solve this problem, GearUp’s JavaScript library can perform a token exchange using the external Air0 ID token as the input. This results in an Auth0 access token that is generated and associated with the corresponding GearUp user based on their email address. Once the GearUp library gets the access token, it can start using GearUp’s APIs to offer car rental services directly within Air0’s website.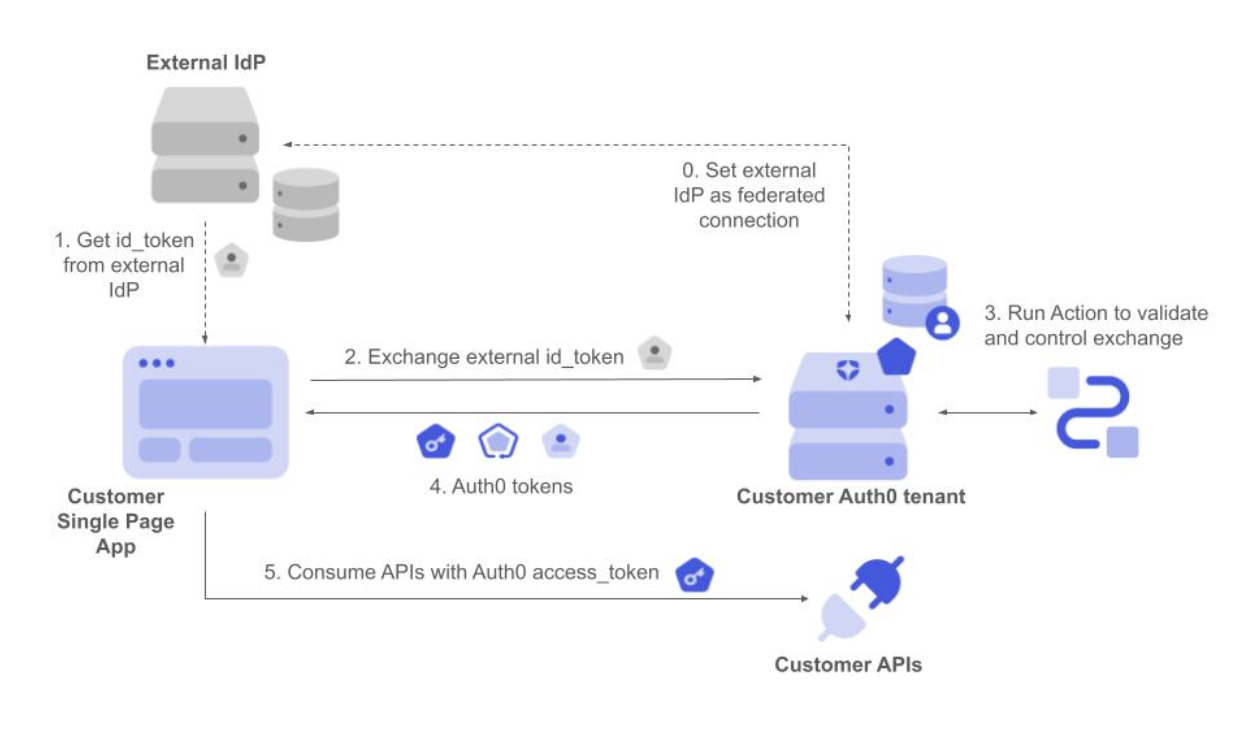
- The Single Page App gets the ID token from the external IdP once the user authenticates.
- It then requests the exchanges of the ID token, setting it as the subject token.
- The corresponding Custom Token Exchange profile Action executes. It validates the ID token and gets the user ID and other profile attributes from the token. It then applies the required authorization policy and finally sets the user.
- Auth0 responds with Auth0 access token, ID token and refresh token.
- The javascript code running in the SPA can now use the Customer APIs using Auth0 tokens without the user having to re-authenticate.
- We use the external IdP user ID to set the user in the corresponding connection.
- We want to create the user if they don’t yet exist.
- We don’t want to replace the user profile if a more complete set of attributes is obtained via federated login, in case the user already exists.
- We don’t want to verify emails when users are created.
Use Case: Get Auth0 tokens for another audience
GearUp wants to improve how it authorizes calls between its internal microservices to serve API requests. It wants a centralized policy controlling the resources that each service can consume. This can also be solved using Token Exchange. When the API request first arrives at service A, it exchanges the received access token for a new one that allows it to consume service B as the new audience. If the authorization policy governing the token exchange allows it, service A gets the new token back and can now consume service B. The user ID is kept unchanged in the new token, so the proper user context is retained throughout the process.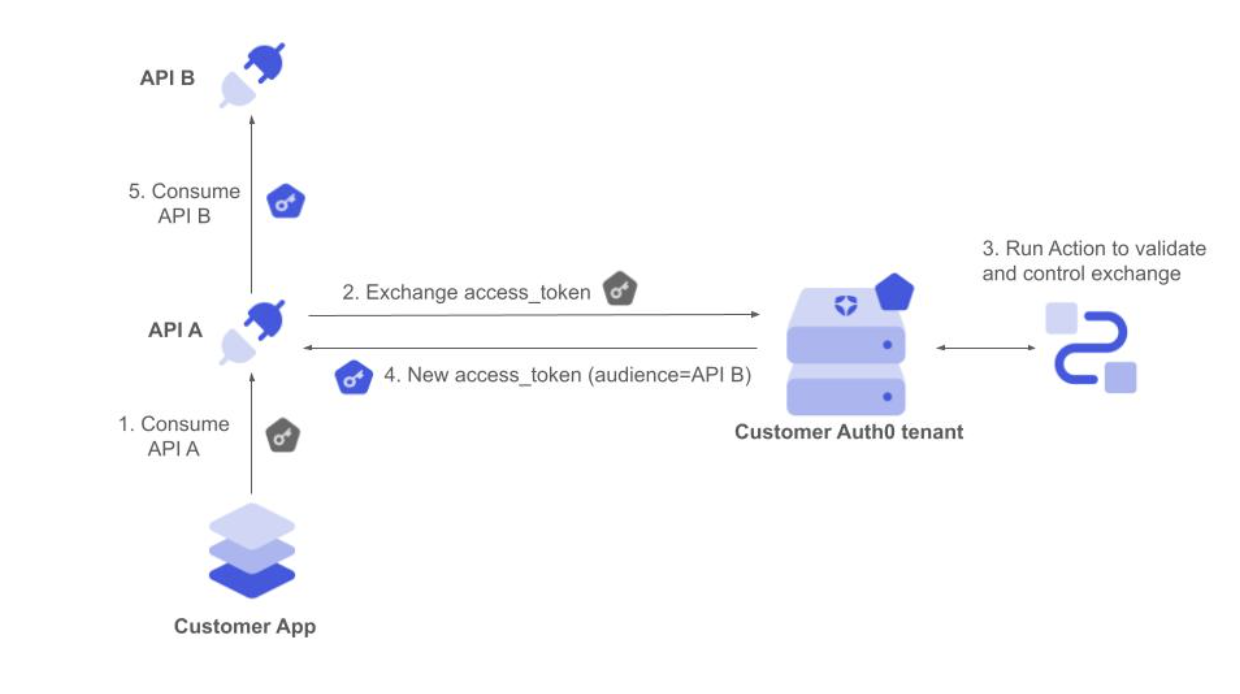
- The app sends the request with the initial access token to API A.
- API A backend service validates the access token and requests to exchange by setting it as the subject token for a new access token to consume API B.
- The corresponding Custom Token Exchange profile Action executes. It validates the access token and gets the Auth0 user ID from the token. It then applies the required authorization policy and finally sets the user.
- Auth0 responds with an Auth0 access token to consume the API B audience.
- API A backend service calls API B using the new access token, which is still associated with the same user.
- We use the Auth0 user ID to set the user, so there is no need to set this in the scope of any connection.
- We don’t want to create or update the user.
Code samples
The following code samples show best practices for common scenarios for validating incoming subject tokens in a secure and performant way. Use asymmetric algorithms and keys whenever you can as you don’t need to share any secret with Auth0. This also simplifies key rotation, such as when exposing a JWKS URI endpoint to advertise applicable public keys.It is your responsibility to ensure that subject tokens are protected with a strong algorithm and keys/secrets with enough entropy.
Validate JWTs signed with asymmetric keys
Consider the following recommendations:- Use Actions api.cache methods to avoid having to fetch the signing keys for each transaction.
- Adhere to RFC8725 best practices
- Use RS*, PS*, ES* or Ed25519 algorithms
- Do not use or accept the none algorithm
- Use RSA with a minimum length of 2048 bits.
Validate JWTs signed with symmetric keys
Consider the following recommendations:- Use Actions Secrets to securely store your symmetric secrets.
- Adhere to RFC8725 best practices
- Use secure algorithms such as HS256, along with high entropy random secrets (e.g. of at least 256 bits long)
Validate opaque token with an external service
Use Action Secrets to securely store your external IdP .Limitations
This is an Early Access feature and thus comes with some limitations and incompatibility with other Auth0 features. The following features are not supported (or will not work properly) with Custom Token Exchange EA:- Organizations
- :
api.authentication.challengeWith()andapi.multifactor.enable()commands in Post Login actions are not yet supported for Custom Token Exchange and will result in the transaction failing with a non-recoverable error; similarly, transactions will also fail when MFA is configured as a tenant policy - Custom DB Connections with Import Users to Auth0 enabled are not supported for
setUserByConnection()operations - Specific impersonation support (e.g. actor token and actor claim)
- Third-Party and Non-OIDC Conformant Clients
Rate Limits
Custom Token Exchange requests to the/oauth/token endpoint are rate limited at 10% of the global Authentication API rate limit for the applicable performance tier.
| Performance Tier | Global Authentication API limit (RPS) | Custom Token Exchange limit (RPS) |
|---|---|---|
| Enterprise | 100 | 10 |
| Private Cloud Basic (1x) | 100 | 10 |
| Private Cloud Performance (5x) | 500 | 50 |
| Private Cloud Performance (15x) | 1500 | 150 |
| Private Cloud Performance (30x) | 3000 | 300 |
| Private Cloud Performance (60x) | 6000 | 600 |
| Private Cloud Performance (100x) | 10000 | 1000 |
api/v2/token-exchange-profiles endpoints are also rate limited as follows:
| Performance Tier | Custom Token Exchange limit (RPS) | Custom Token Exchange limit (RPM) |
|---|---|---|
| Enterprise | 20 | 200 |
| Private Cloud Basic (1x) | 20 | 200 |
| Private Cloud Performance (5x) | 100 | 300 |
| Private Cloud Performance (15x) | 300 | 3000 |
| Private Cloud Performance (30x) | 600 | 6000 |
| Private Cloud Performance (60x) | 1200 | 12000 |
| Private Cloud Performance (100x) | 2000 | 20000 |
Entity Limits
A maximum of 100 Custom Token Exchange profiles can be created per tenant. The total number of Actions is also limited depending on your Auth0 plan. To learn more, read Auth0’s Pricing Page.Troubleshoot
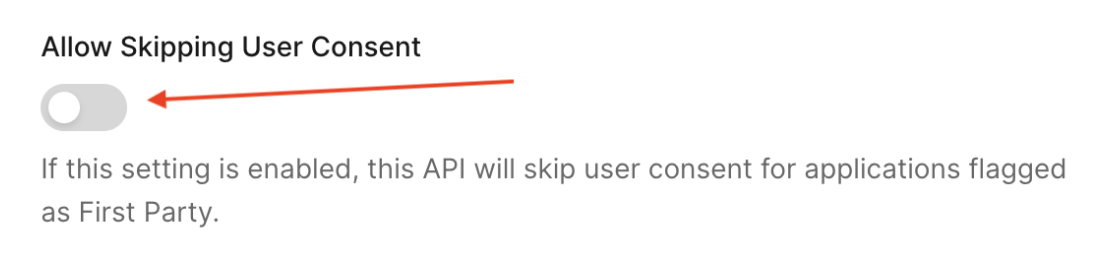
”Consent required” response
You may receive aninvalid_request error with a consent_required error description when calling the /oauth/token endpoint.
To resolve this issue, enable the Allow Skipping User Consent option for your API in the Auth0 Dashboard.