Configure your Vault connection
To configure a Vault connection for your JSON Web Token actions using HS256 algorithm, you will need a Secret: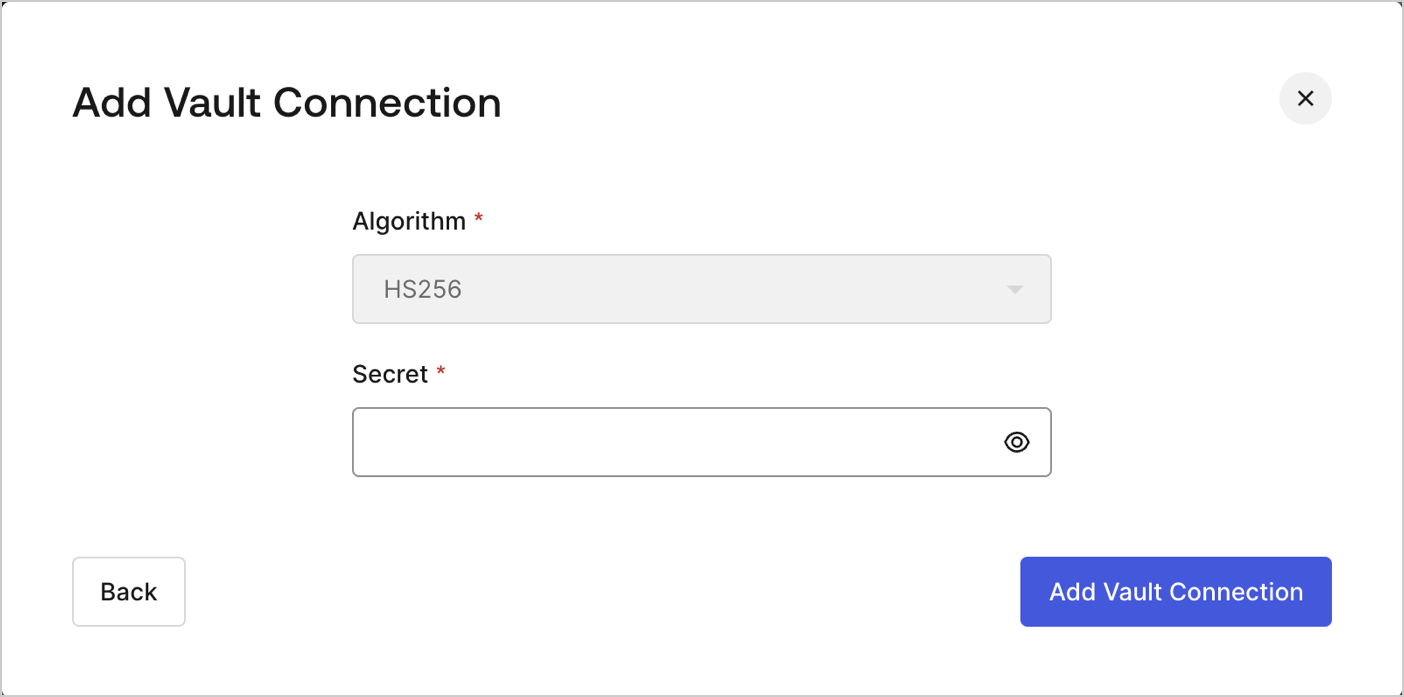
Sign JSON web token
Generates a JSON web token.
Input settings
| Parameter | Description |
|---|---|
| Payload | Data to encode. We recommend to format it according to OpenID standards. |
| Subject | Identifies the subject of the JWT. |
| Issuer | Identifies principal that issued the JWT. |
| Audience | Identifies the recipients that the JWT is intended. For example: admin.your_domain.com |
| Expires in | Identifies the expiration time on and after which the JWT must not be accepted for processing. |
Output object
| Property | Type | Description |
|---|---|---|
token | String | A JSON web token string. |
Output object example
Decode JSON web token
Decodes a provided JSON web token.
Input settings
| Parameter | Description |
|---|---|
| Token (required) | JSON web token string that will be decoded. |
Output object
| Property | Type | Description |
|---|---|---|
payload | object | The decoded and valid JSON web token content |
Output object example
Verify JSON web token
Verifies the JSON web token data, to determine if it remains intact or has been modified, in order to guarantee its authenticity.
Input settings
| Parameter | Description |
|---|---|
| Token (required) | JSON web token string that will be verified. |
| Issuer | The issuer of the JWT that will be verified. |
| Audience | The recipient audience of the JWT is intended that will be verified. |
Output object
| Property | Type | Description |
|---|---|---|
valid | Boolean | Returns true or false depending on whether or not the JWT has a valid signature. |
cause | String | If the valid property is false a message is displayed. |
payload | Object | The decoded and valid JSON web token content. |

