Use the Dashboard
-
Go to Dashboard > Applications > APIs and click the name of the API to view.
-
Go to the Permissions tab and enter a permission name and description for the permission you want to add. Be sure not to use any reserved permission names (see Reserved names section).
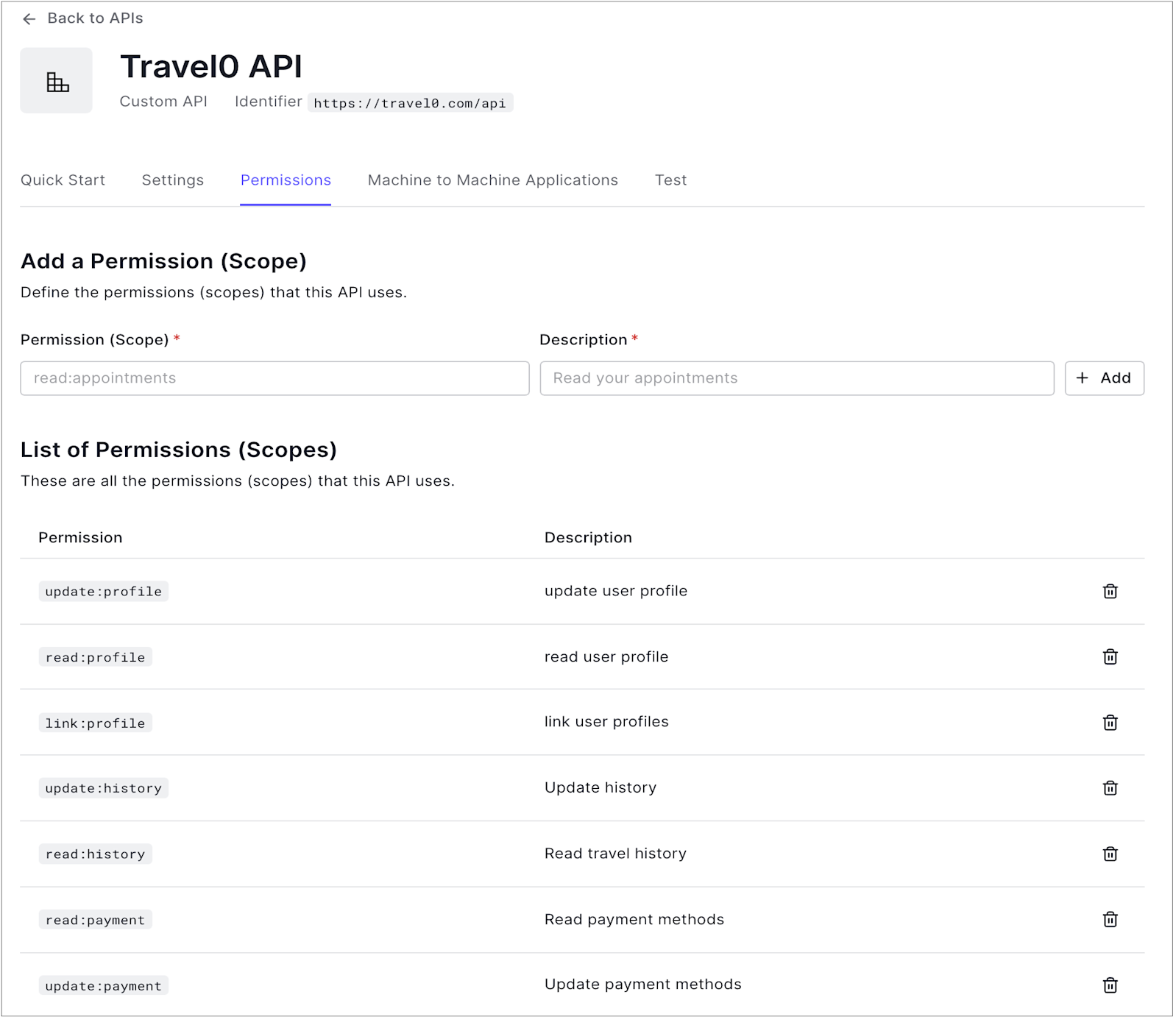
- Click Add. Remember that individual Applications may need permissions and/or scopes updated to interact properly with the API.
Use the Management API
Patching the permissions with an empty object removes the permissions completely.
PATCH call to the Update Resource Server endpoint. Be sure to replace API_ID, MGMT_API_ACCESS_TOKEN, PERMISSION_NAME, and PERMISSION_DESC placeholder values with your API ID, Management API , permission name(s), and permission description(s), respectively. Be sure not to use any reserved permission names (see Reserved names section).
When adding or updating scopes, Management API requires that you pass all scopes you would to include. If any of the existing scopes are not passed, they will be removed.
| Value | Description |
|---|---|
API_ID | ID of the API for which you want to delete permissions. |
MGMT_API_ACCESS_TOKEN | Access Token for the Management API with the scope update:resource_servers. |
PERMISSION_NAME | Name(s) of the permission(s) you want to keep for the specified API. |
PERMISSION_DESC | User-friendly description(s) of the permission(s) you want to keep for the specified API. |
Reserved names
The following permission names are reserved and cannot be set as custom API permissions:- address
- created_at
- email_verified
- family_name
- given_name
- identities
- name
- nickname
- offline_access
- phone
- picture
- profile

