API Authentication and Authorization
An API is a way to expose functionality of your application to other applications. An application can make a request by sending a message to an endpoint on an API and receive information as a response. An API endpoint can be secured or not. In our case, since the timesheets are sensitive information that affect reviews and payments, it is important to ensure that only authorized users and applications can call the endpoints on our API. When a client application wants to access protected endpoints on an API, it needs to present an as proof that it has the required permissions for making the call to the endpoint. An Access Token is obtained by authenticating the user with an and the user can then, in turn, authorize the application to access the API on their behalf.What is an Access Token?
An Access Token (also referred to as
access_token) is an opaque string representing an authorization issued to the application. It may denote an identifier used to retrieve the authorization information or may self-contain the authorization information (for example, the user’s identity, permissions, and so forth) in a verifiable manner.It is quite common for Access Tokens to be implemented as JSON Web Tokens.For more information on Auth0 Access Tokens refer to Access Token.scope claim.
Subsequently, when the client passes along the Access Token when making requests to the API, the API can inspect the scope claim to ensure that the required permissions were granted in order to call the particular API endpoint.
What are Scopes?
Each Access Token may include a list of the permissions that have been granted to the client. When a client authenticates with Auth0, it will specify the list of scopes (or permissions) it is requesting. If those scopes are authorized, then the Access Token will contain a list of authorized scopes.For example, the timesheet API may accept four different levels of authorization: reading timesheets (scope
read:timesheets), creating timesheets (scope create:timesheets), deleting timesheets (scope delete:timesheets) and approving timesheets (scope approve:timesheets).When a client asks the API to create a new timesheet entry, then the Access Token should contain the create:timesheets scope. In a similar fashion, in order to delete existing timesheets, the Access Token should contain the delete:timesheets scope.For more information on scopes refer to Scopes.OAuth roles
In any OAuth 2.0 flow we can identify the following roles:
- Resource Owner: the entity that can grant access to a protected resource. Typically this is the end-user.
- Resource Server: the server hosting the protected resources. This is the API you want to access.
- Client: an application requesting access to a protected resource on behalf of the Resource Owner.
- Authorization Server: the server that authenticates the Resource Owner, and issues Access Tokens after getting proper authorization. In this case, Auth0’s Authentication API.
Proof Key for Code Exchange (PKCE)
OAuth 2 provides several grant types for different use cases. In this particular use case, we want to access the API from a mobile application, which will use the Authorization Code Flow with Proof Key for Code Exchange (PKCE) to do so. The Authorization Code Flow has some security issues when implemented on native applications. For instance, a malicious attacker can intercept theauthorization_code returned by Auth0 and exchange it for an Access Token (and possibly a Refresh Token).
The Proof Key for Code Exchange (PKCE) (defined in RFC 7636) is a technique used to mitigate this authorization code interception attack.
With PKCE, the Application creates, for every authorization request, a cryptographically random key called code_verifier and its transformed value called code_challenge, which is sent to Auth0 to get the authorization_code. When the Application receives the authorization_code, it will send the code and the code_verifier to Auth0’s to exchange them for the requested tokens.
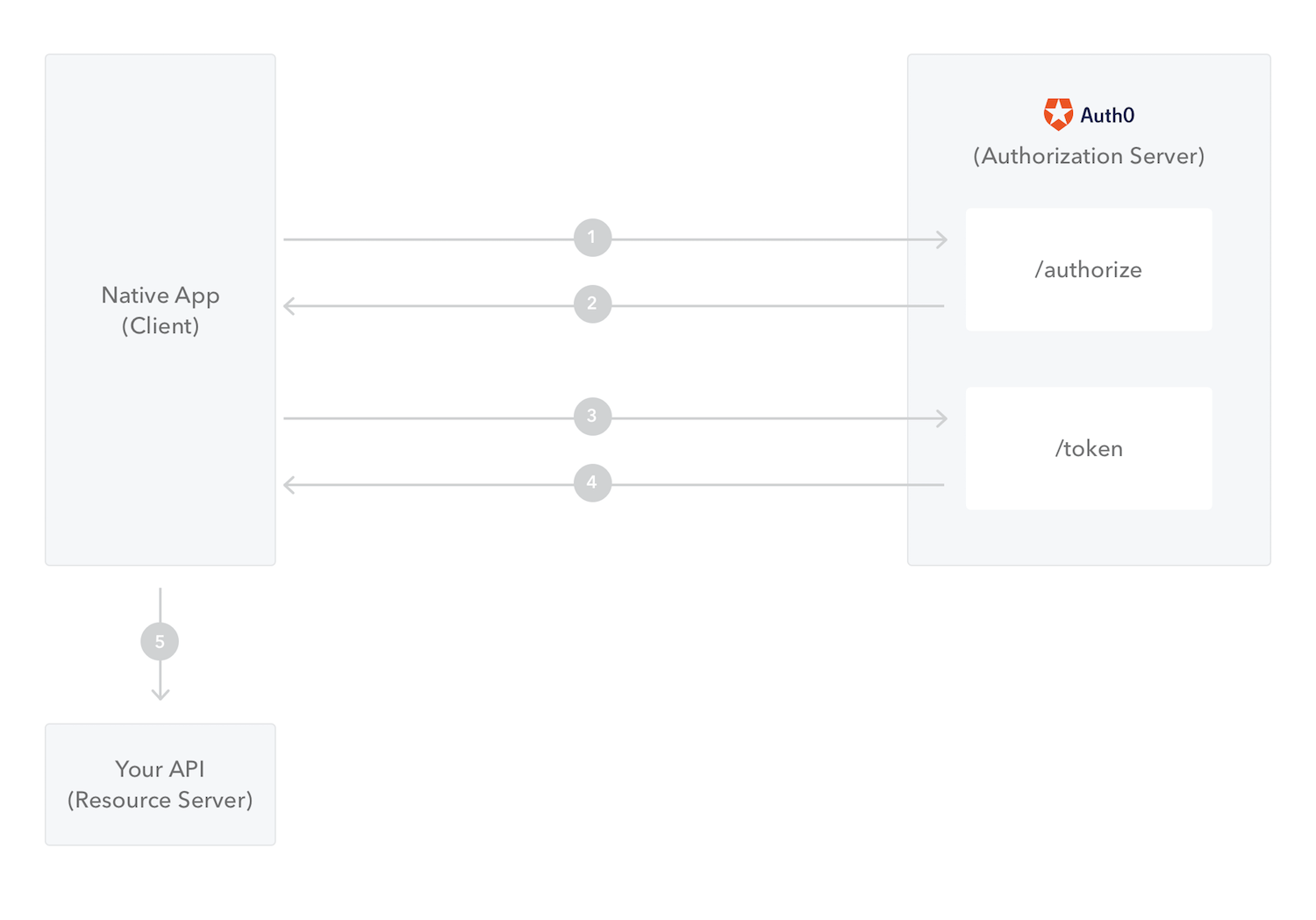
- The native app initiates the flow and redirects the user to Auth0 (specifically to the /authorize endpoint), sending the
code_challengeandcode_challenge_methodparameters. - Auth0 redirects the user to the native app with an
authorization_codein the query string. - The native app sends the
authorization_codeandcode_verifiertogether with theredirect_uriand theclient_idto Auth0. This is done using the /oauth/token endpoint. - Auth0 validates this information and returns an Access Token (and optionally a Refresh Token).
- The native app can use the Access Token to call the API on behalf of the user.
If you have Refresh Token Rotation enabled, a new Refresh Token is generated with each request and issued along with the Access Token. When a Refresh Token is exchanged, the previous Refresh Token is invalidated but information about the relationship is retained by the authorization server.

