How it works
For a native app, the Sign in with Apple login flow works as follows: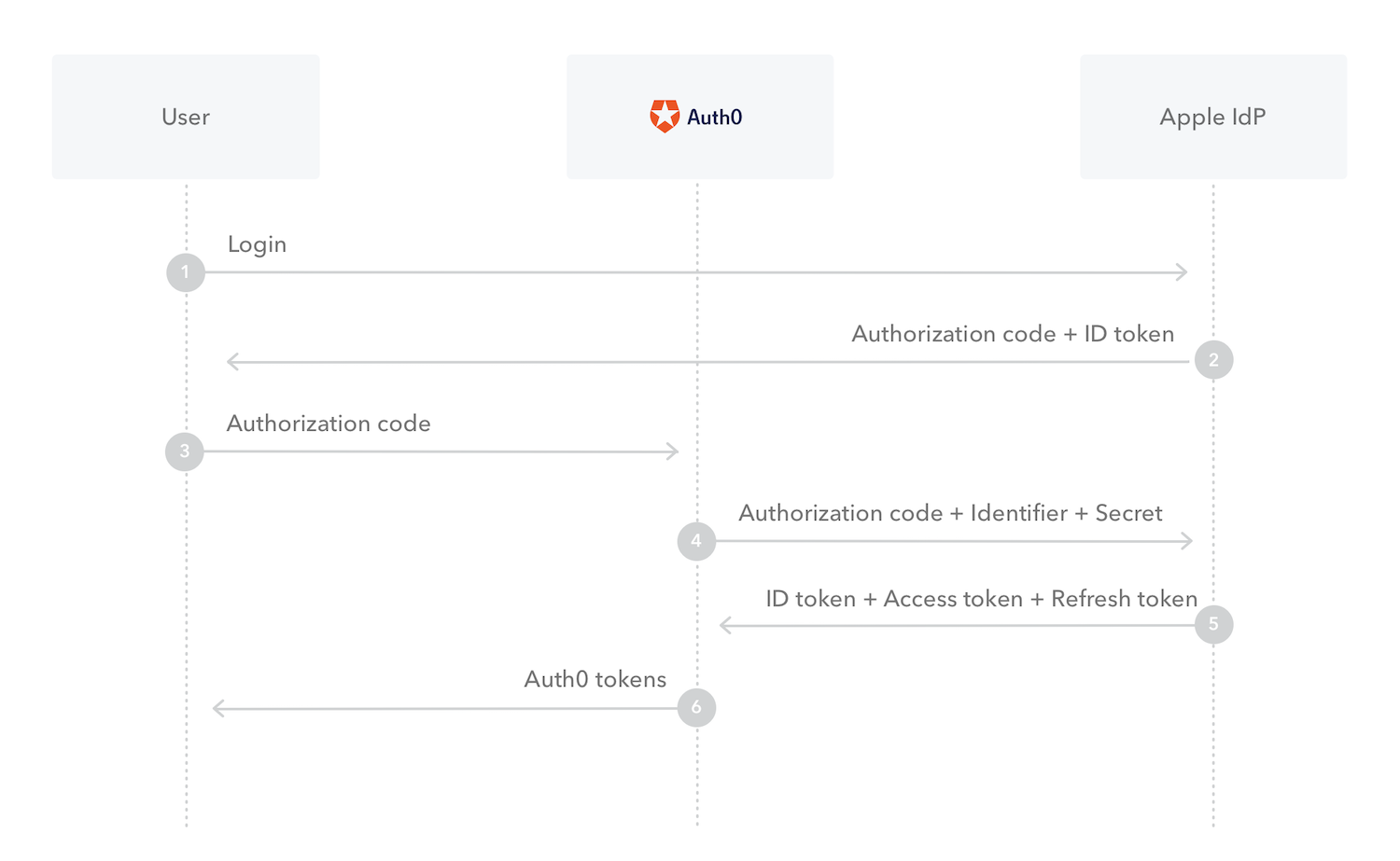
- Steps 1 & 2: User authenticates via Apple’s SDK on their iOS device, and receive an authorization code in the response. The user does not have to leave the app and use a browser to log in.
-
Step 3: The application calls Auth0’s
/oauth/tokenendpoint to exchange the Apple authorization code for Auth0 tokens. - Step 4 & 5: The Auth0 platform exchanges the Authorization code with Apple for tokens. Auth0 validates the tokens, and uses the claims in the tokens to construct the identity of the user.
- Step 6: Auth0 saves the user profile, executes rules and authorization, then issues Auth0 ( and ) as requested. These tokens are used to protect your APIs and users managed by Auth0.
Prerequisites
Before you configure Sign In with Apple for your native app in Auth0, you must:- Have an Apple Developer account, which is a paid account with Apple. (There is no free trial available unless you are part of their iOS Developer University Program.)
-
Register Your App in the Apple Developer Portal if you have not already done so. Make a note of the following IDs and key for the application connection settings in the :
- App ID
- Apple Team ID
- Client Secret Signing Key
- Key ID
-
If you are using the Classic Login flow or embedding
Lock.jsin your application, make sure you are usingLock.jsversion 11.16 or later.
Configure and enable the connection in Auth0
Once you have the credentials you need from your Apple Developer account, you need to configure the application client and the connection settings in Auth0.- Navigate to Auth0 Dashboard > Applications > Applications, choose your application, and select the gear icon to view the settings page.
-
At the bottom of the page, select Show Advanced Settings and then the Device Settings view. Under Native Social Login, enable the Enable Sign In with Apple toggle.
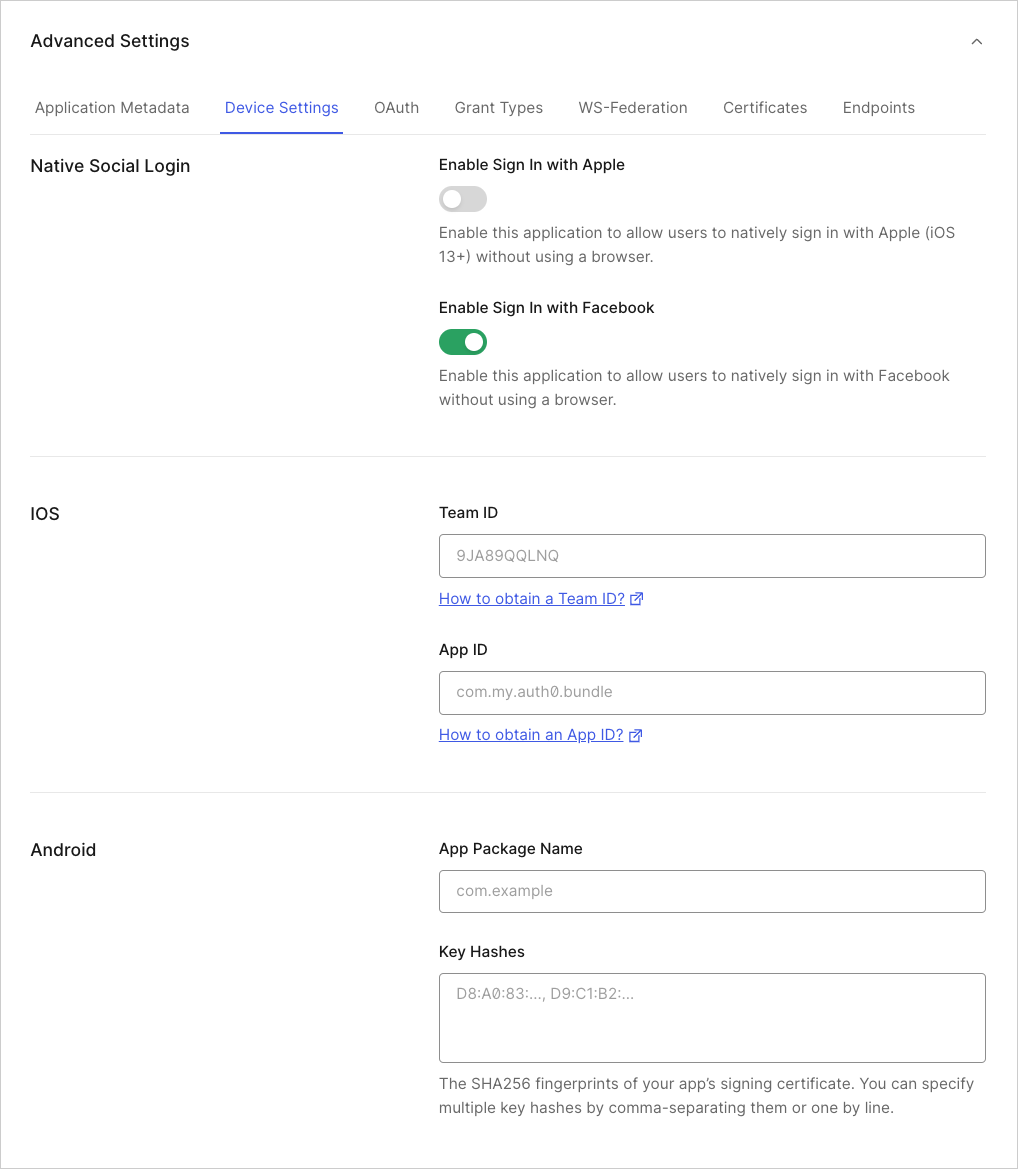
- Under iOS, fill in the App ID field with the native app’s App ID/Bundle Identifier.
- Navigate to Auth0 Dashboard > Authentication > Social, and select Create Connection.
- Select the Apple connection and consent.
-
On the Settings tab, fill in the following fields:
- Apple Team ID
- Client Secret Signing Key
-
Key ID
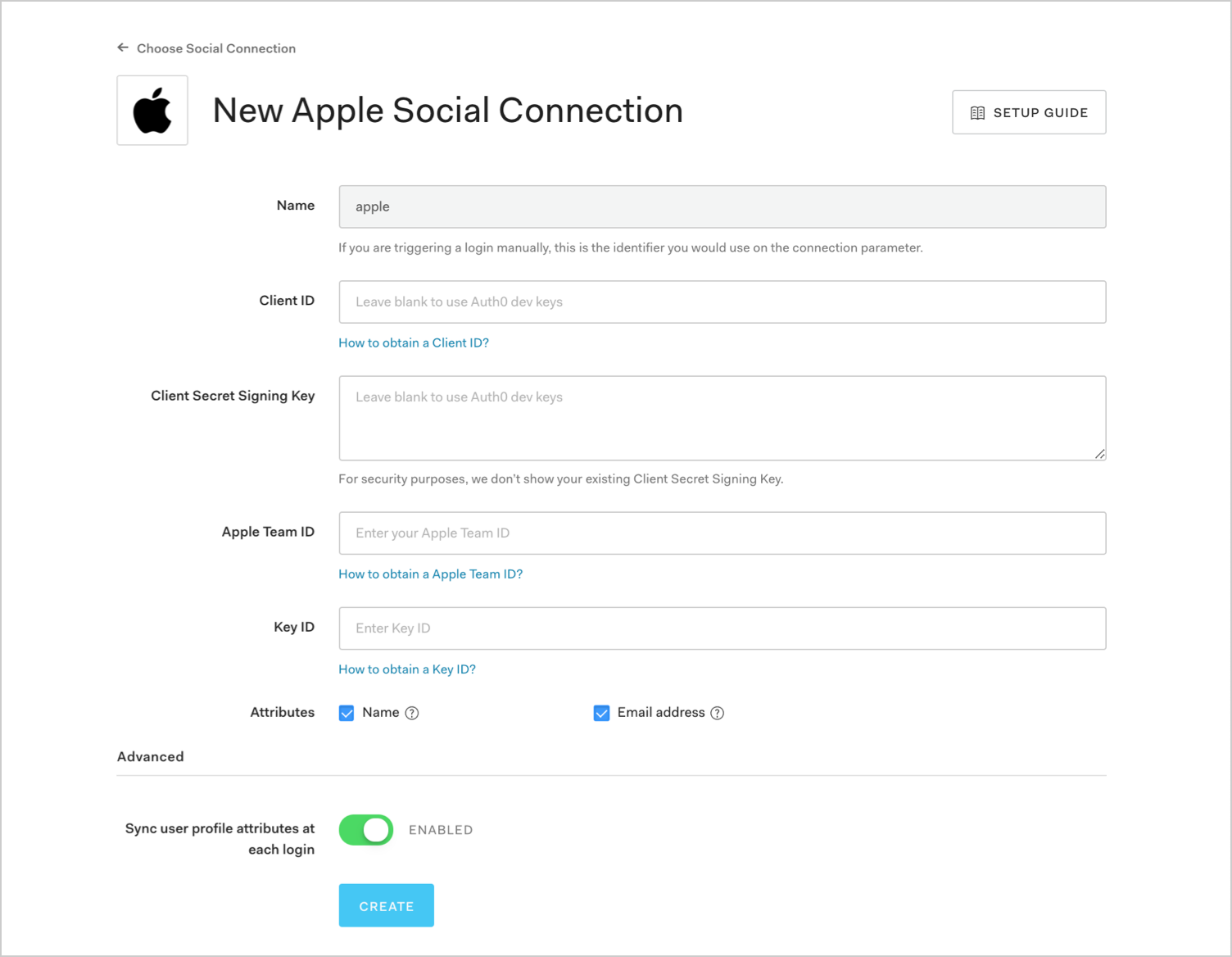
- Select the Applications view to enable this connection for your application.
- Click Save.
Native apps cannot be tested from the browser. This means that the Try Connection button on the Apple connection is used exclusively for testing web-based flows.
Logout
Since the Native iOS login implementation does not make use of standard browser-based flows, application owners must also take care to perform logout appropriately. When an application needs to perform a logout, it must take the following actions:- Revoke the Auth0 Refresh Token
- Delete the Auth0 refresh token stored in the iCloud Keychain
- Delete the Apple user identifier stored in the iCloud keychain Also, keep in mind that logout can result from user actions (for example, clicking a “log out” button) or from a user revoking access to the given app. The latter will be indicated through the native ASAuthorizationAppleIDProvider.getCredentialState method.
One nuance of Apple’s IdP is that it only returns requested scopes (such as email, first name, and last name) in the ID token on the first response. More destructive approaches to logout (such as deleting the user) could result in loss of profile information, which would require end users to deauthorize and reauthorize an app.

