Auth0 recommends WebAuthn factors as the most secure and usable authentication methods. To learn more, read FIDO Authentication with WebAuthn.
Add MFA
To self-enroll for MFA, each Dashboard user must follow these steps:- Click on your username in the top right corner of the Dashboard and click Your Profile.
-
Find the supported method you want and click + ADD in that row.
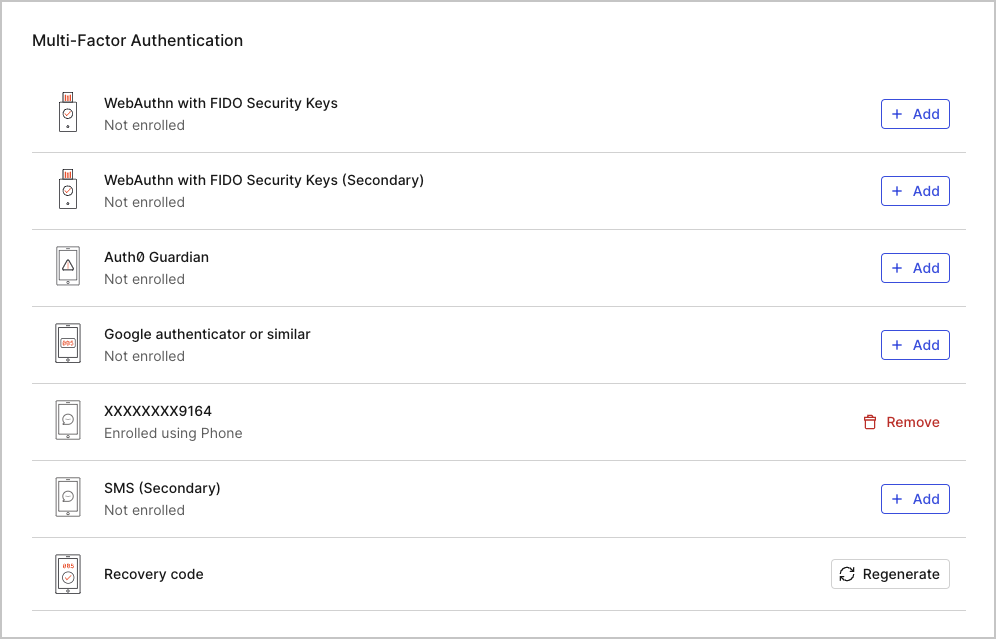
- Follow the on-screen instructions to complete the enrollment.
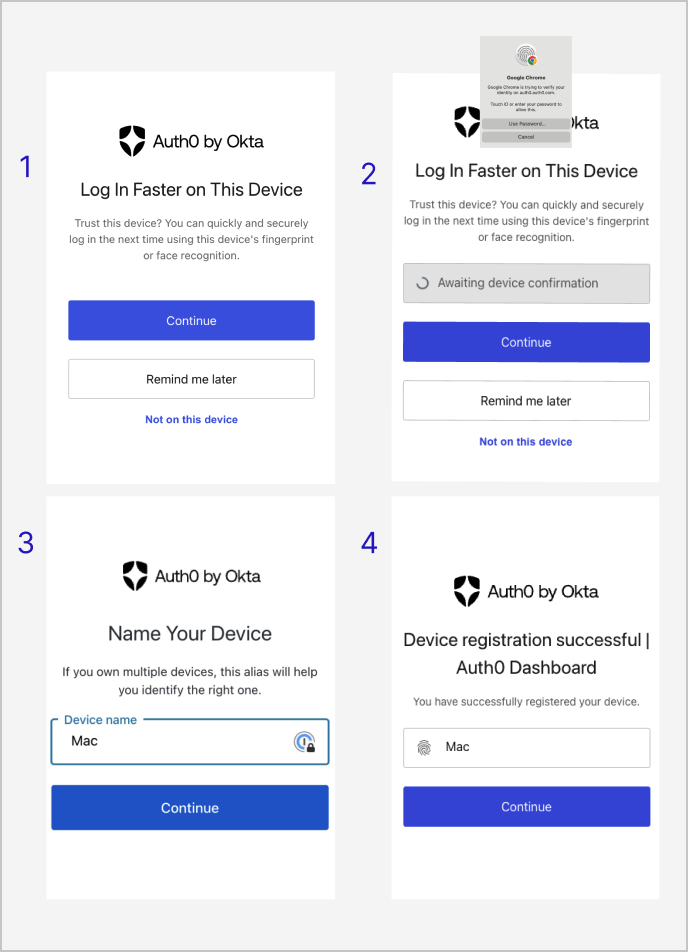
Device biometrics
WebAuthn with device biometrics is the only method that you can’t add on the Account Settings page. Instead, Auth0 progressively enrolls all of your WebAuthn-capable devices. Auth0 prompts you to enroll those devices after you enroll any other MFA method. These prompts recur each time you log in to Auth0 Dashboard.