Auth0 allows you to add authentication and access user profile information in almost any application type quickly.
This guide demonstrates how to integrate Auth0 with any new or existing ASP.NET Web API application using the
Microsoft.AspNetCore.Authentication.JwtBearer package.If you haven’t created an API in your Auth0 dashboard yet, you can use the interactive selector to create a new
Auth0 API or select an existing API that represents the project you want to integrate with.Alternatively, you can read our getting started guide,
which will help you set up your first API through the Auth0 Dashboard.Note that every API in Auth0 is configured using an API Identifier; your application code will use the API
Identifier as the Audience to validate the access token.New to Auth0? Learn how Auth0 works and
read about implementing API authentication and
authorization using the OAuth 2.0 framework.
1
Define permissions
Permissions let you define how resources can be accessed on behalf of the user with a given access token. For
example, you might choose to grant read access to the 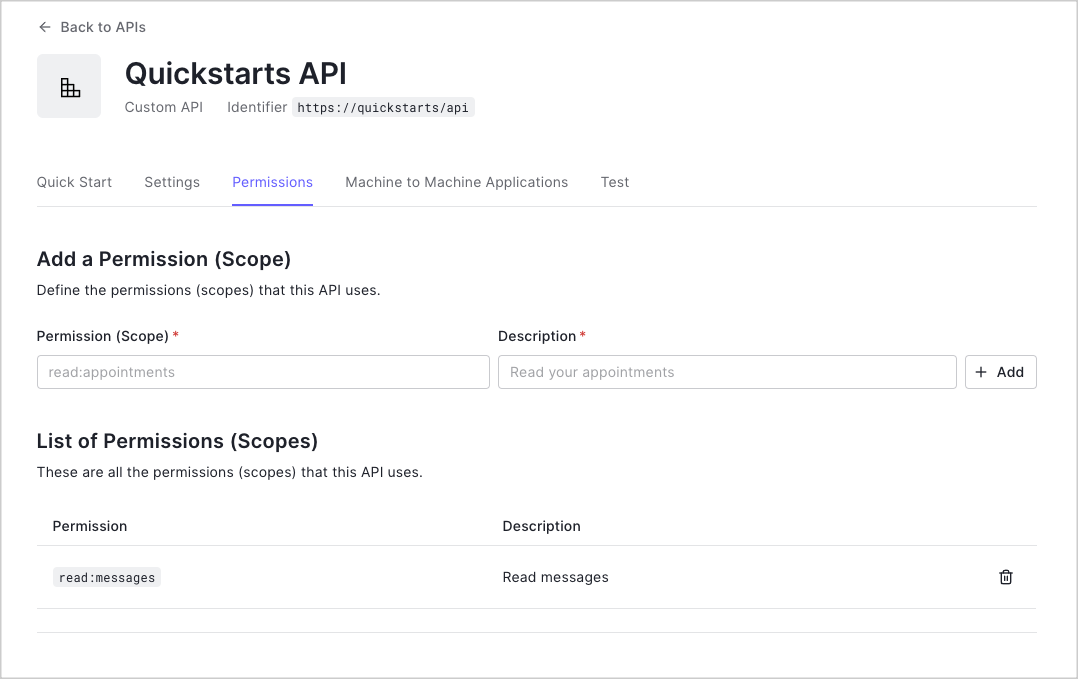
messages resource if users have the manager
access level, and grant write access to that resource if they have the administrator access level.You can define allowed permissions in the Permissions view of the Auth0 Dashboard’s APIs section. The following
example uses the read:messages scope.
2
Install dependencies
To allow your application to validate access tokens, add a reference to the
Microsoft.AspNetCore.Authentication.JwtBearer NuGet package:3
Configure the middleware
Set up the authentication middleware by configuring it in your application’s
Program.cs file:-
Register the authentication services by making a call to the
AddAuthenticationmethod. ConfigureJwtBearerDefaults.AuthenticationSchemeas the default scheme. -
Register the JWT Bearer authentication scheme by making a call to the
AddJwtBearermethod. Configure your Auth0 domain as the authority and your Auth0 API Identifier as the audience, and be sure that your Auth0 domain and API Identifier are set in your application’s appsettings.json file.In some cases, the access token will not have asubclaim; in this case, theUser.Identity.Namewill benull. If you want to map a different claim toUser.Identity.Name, add it tooptions.TokenValidationParameterswithin theAddJwtBearer()call. -
Add the authentication and authorization middleware to the middleware pipeline by adding calls to the
UseAuthenticationandUseAuthorizationmethods under thevar app = builder.Build();method.
4
Validate scopes
To ensure that an access token contains the correct scopes, use Policy-Based Authorization in the ASP.NET Core:
- Create a new authorization requirement called
HasScopeRequirement, which will check whether thescopeclaim issued by your Auth0 tenant is present, and if so, will check that the claim contains the requested scope. - Under your
Program.csfile’svar builder = WebApplication.CreateBuilder(args);method, add a call to theapp.AddAuthorizationmethod. - Add policies for scopes by calling
AddPolicyfor each scope. - Register a singleton for the
HasScopeHandlerclass.
5
Protect API endpoints
The JWT middleware integrates with the standard ASP.NET Core Authentication and Authorization mechanisms.To secure an endpoint, add the
[Authorize] attribute to your controller action (or the entire
controller if you want to protect all of its actions).When securing endpoints that require specific scopes, make sure that the correct scope is present in the
access_token. To do so, add the Authorize attribute to the Scoped action
and pass read:messages as the policy parameter.6
Call your API
The way in which you call your API depends on the type of application you are developing and the framework you
are using. To learn more, read the relevant application Quickstart:Example requestCall the
Get an access token
Regardless of the type of application you are developing or the framework you are using, to call your API, you need an access token.If you call your API from a Single-Page Application (SPA) or Native application, you will receive an access token after the authorization flow completes.If you call the API from a command-line tool or other service where a user entering credentials does not exist, use the OAuth Client Credentials Flow. To do so, register a Machine-to-Machine Application and pass the following values in your request:- Client ID as the
client_idparameter. - Client Secret as the
client_secretparameter. - API Identifier (the same value used to configure the middleware earlier in this quickstart) as the
audienceparameter.
To learn more about getting the Client ID and Client Secret for your machine-to-machine application,
read Application Settings.
Call a secure endpoint
Now that you have an access token, you can use it to call secure API endpoints. When calling a secure endpoint, you must include the access token as a Bearer token in the Authorization header of the request. For example, you can make a request to the/api/private endpoint:/api/private-scoped endpoint in a similar way, but ensure that the API permissions are
configured correctly and that the access token includes the read:messages scope.Checkpoint
You should now be able to call the/api/private and /api/private-scoped
endpoints.Run your application and verify that:GET /api/privateis available for authenticated requests.GET /api/private-scopedis available for authenticated requests containing an access token with theread:messagesscope.
Next Steps
Excellent work! If you made it this far, you should now have login, logout, and user profile information running in your application.This concludes our quickstart tutorial, but there is so much more to explore. To learn more about what you can do with Auth0, check out:- Auth0 Dashboard - Learn how to configure and manage your Auth0 tenant and applications
- Auth0 Marketplace - Discover integrations you can enable to extend Auth0’s functionality


























